Explainer Video
Zero Trust Architecture
The Zero Trust approach is based on the principle of no trust by default. The goal is to allow access only to authorized users, using multiple layers of security and advanced solutions that ensure that access is secure and based on limited permissions. Below are the core components of the Zero Trust architecture with an emphasis on secure access:
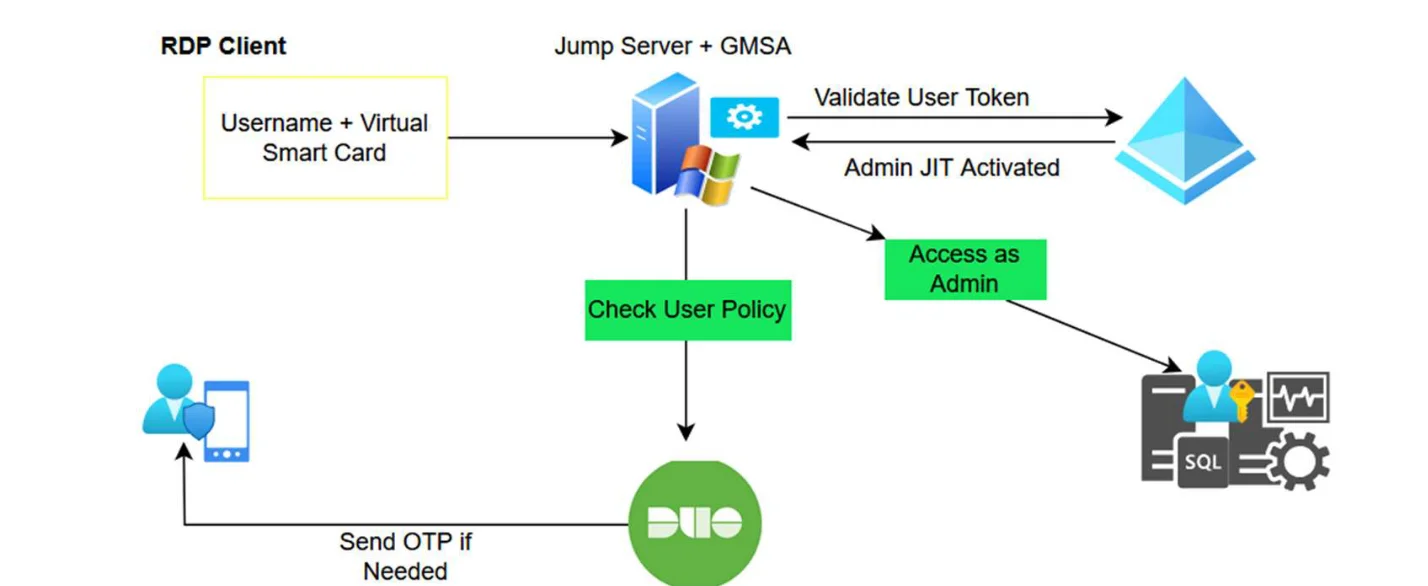
Core Components:
-
Strong authentication and access based on TPM, Virtual Smartcard, and Duo
Use of Virtual Smartcard, which is based on a hardware-based TPM module that is secure against counterfeiting. Duo adds an additional layer of two-step authentication (2FA) which ensures that the authentication process will be performed only by the authorized user. Remote access (RDP) is made possible in a secure manner using these tools, which ensures the preservation of information and protection against unauthorized access.
-
Temporary access with Just-In-Time (JIT) Domain Admin
As part of the Zero Trust principles, temporary access management based on Just-In-Time (JIT) grants users administrative permissions for limited periods of time only. This solution allows granting access to domain management (JIT Domain Admin) or local management (JIT Local Admin) only when necessary and for a limited time. Access is secured using digital certificates for identity management, and ensures that every connection is made in an encrypted and controlled manner.
Assume Breach Architecture
The Assume Breach approach is based on the assumption that attackers have already entered the system. In this model, the infrastructure is built in such a way that it enables rapid identification, containment, and response to threats, and is based on the following protection principles:
Protection Principles:
-
Identification of vulnerabilities and threats
The system focuses on identifying any suspicious activity using advanced monitoring and analysis tools, such as SIEM and XDR, in order to identify threats at an early stage and alert the security teams.
-
Restricting access as needed
The Assume Breach model incorporates minimal access controls, which grant permissions only to those who really need them. This principle prevents the expansion of an attack in the event of a system penetration.
-
Isolation of sensitive areas (Segmentation)
Separation of networks and applications that are essential for independent segments, so that attackers will not be able to advance in the system in the event of a breach. Each area is protected with specific security controls.
Fast and automatic response
In the event of a breach being detected, the system activates a rapid response, which includes blocking access, isolating infected stations, and taking immediate steps to prevent the spread. The architecture of Assume Breach ensures that if attackers have indeed penetrated the system, the organization will be able to respond effectively, isolate the threat and prevent further damage quickly and in a controlled manner.
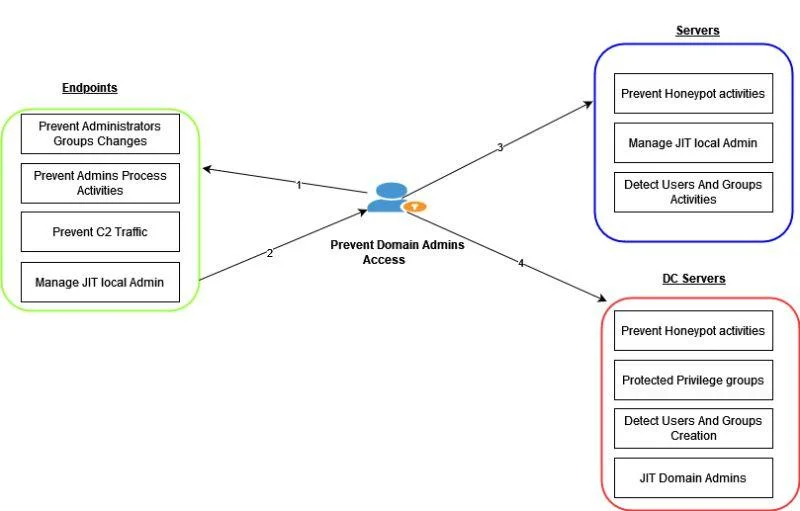
Automation at Endpoints
Preventing changes to the administrators group
Goal: to maintain the integrity of the group of administrators at the endpoints. How it works: If a new user is added to the administrator group (whether intentionally or unintentionally), the system will identify the change and automatically remove the new user.
Preventing unauthorized administrator actions
Goal: to prevent unauthorized administrator processes from running on endpoints. How it works: Any process with administrator permissions, which is not recognized or suspicious, will be identified and stopped automatically. It is also possible to disconnect the endpoint from the network or restart it according to the threat.
Preventing domain admin at endpoints
Goal: to prevent domain administrator permissions from being part of the local administrators group at the endpoints. How it works: Domain administrator permissions cannot be part of the group of administrators at the endpoints, which prevents potential attacks on the station from spreading to the entire domain.
Preventing Command and Control (C2) traffic
Goal: to block malicious traffic that uses a connection to external servers. How it works: Automation identifies unsigned files that try to connect to the network and blocks access automatically.
Temporary local admin management (JIT)
Goal: to limit the access of administrators only to times when it is necessary. How it works: Admin users are created with temporary access only (Just-In-Time). After the set period of time has expired, the account is neutralized and the password is changed.
Automation on Servers
Preventing Honeypot activities
Goal: creating dummy accounts whose purpose is to identify attacks by attracting attackers. How it works: Automation creates dummy accounts on servers that cannot perform real actions, but appear to attackers as legitimate accounts.
Identifying user and group activities
Goal: to monitor and prevent unauthorized changes to user accounts and groups on servers. How it works: Any unauthorized change to user or group rights will be detected and reversed.
Automation in Domain Controllers (DCS)
Protecting privileged groups
Goal: to prevent unauthorized addition of users to privileged groups. How it works: Privileged groups such as domain administrators are protected through automation, so that any new user added to these groups will be removed automatically.
Temporary domain admin (JIT)
Goal: to limit the access of domain administrators only when it is required. How it works: Automation enables temporary and managed domain administrator access (Just-In-Time), using gMSA accounts that manage access.
Risks Without Automation-Based Security
Without implementing Assume Breach and Zero Trust strategies, companies may be exposed to a wide range of risks:
Endpoint risks
-
Uncontrolled changes in the admin group
Risk: Attackers can add themselves to the administrators group and gain full access to the system.
-
Unidentified admin processes
Risk: Malicious processes may operate without any detection.
-
Command and Control (C2) traffic
Risk: Attackers can establish external connections for remote control of systems.
Server risks
-
Lack of monitoring of user and group activities
Risk: Unauthorized user changes can lead to a takeover of the server.
Domain Controller (DCs) risks
-
Unprotected privileged groups
Risk: Attackers can add themselves to critical groups such as domain administrators and cause extensive damage.
Frequently Asked Questions
What is Zero Trust?
Zero Trust is a security framework that assumes no user or device should be inherently trusted, regardless of their location. It requires strict verification of every access request, ensuring that only authorized users and devices can access sensitive resources.
What is the Assume Breach model?
The Assume Breach model is a proactive security approach that assumes a breach has already occurred. It focuses on rapid threat detection, containment, and remediation to minimize the impact of security incidents.
How can SmartPT help my organization?
SmartPT offers a range of cybersecurity services, including the implementation of Zero Trust and Assume Breach strategies. We can help you assess your current security posture, identify vulnerabilities, and implement automated solutions to protect your critical assets.
Contact Us
Ready to enhance your cybersecurity with Zero Trust and Assume Breach strategies? Contact us today for a free consultation.
